
Saffire Pro 10 with Linux
This page describes how to use a Focusrite Saffire Pro 10 I/O with Linux. It also provide general information on setting up JACK and FFADO with Gentoo Linux. The last section describes a JACK client that captures data from the Saffire Pro's eight line-in inputs, then mixes and outputs them using the PC's audio ports (via ALSA).
These instructions were compiled based on the following software versions.
- Linux Kernel: gentoo-sources-2.6.35-r4
- FFADO: 2.0.0
- JACK: 0.118.0


Installing FFADO
The FFADO project provides access to FireWire based audio devices.
Kernel Configuration and Modules
The first step is configuring the kernel to support FireWire. There are two FireWire stacks in the kernel, however as of FFADO version 2.0.0 I've only had success with the older stack.
FFADO make use of the raw1394 kernel module. To allow normal users to access the
module's device node (/dev/raw1394) a simple udev rule can be used to setup
permissions. The rule listed below will provide access to the /dev/raw1394 node for any
user in the 'audio' group. Create this file in the specified location
/etc/udev/rules.d/99-raw1394.rulesKERNEL=="raw1394", GROUP="audio"
Below is the section of kernel configuration that enables the older FireWire stack modules and the raw userspace interface module.
Device Drivers ---> IEEE 1394 (FireWire) support ---> < > FireWire driver stack <M> Legacy alternative FireWire driver stack <M> OHCI-1394 controllers < > PCILynx controller < > Storage devices (SBP-2 protocol) < > IP networking over 1394 (experimental) <M> raw1394 userspace interface < > video1394 userspace interface < > dv1394 userspace interface (deprecated) [ ] Excessive debugging output
After compiling the kernel modules (and perhaps a reboot) you should be able to see the raw userspace module device node with the correct permissions. Try listing the node to check.
> ls -l /dev/raw1394
crw-rw---- 1 root audio 171, 0 Sep 23 08:37 /dev/raw1394
Compiling FFADO
With the kernel all setup, FFADO can now be compiled and installed. The first step is to install the required dependencies. Below is a Gentoo emerge command for the dependencies that are probably not part of a normal Gentoo installation.
> emerge -n libxmlpp libraw1394 libiec61883 scons
The following set of instructions will download, compile and (as super user) install FFADO. The
umask command makes sure files are created with sensible permissions. FFADO is
installed into /usr, this makes the installation of JACK with FFADO support much
easier.
> wget http://www.ffado.org/files/libffado-2.0.0.tar.gz > umask 0022 > tar -zpxf libffado-2.0.0.tar.gz > cd libffado-2.0.0 > scons ENABLE_OPTIMIZATION=True DEBUG=false PREFIX=/usr > su > scons install
If you want to uninstall FFADO, first change to the unpacked source directory and then use the following command.
> scons -c install

Installing and Running JACK
The JACK Audio Connection Kit provides realtime, low latency audio routing. In this case, it give audio applications access to the Saffire Pro via FFADO.
On Gentoo, JACK can be installed using the following emerge command.
> emerge jack-audio-connection-kit
As the compilation text scrolls past, you should be able to see the support for FFADO enabled. Below is an example that shows JACK is being compiled with ALSA and FireWire support.
jack-audio-connection-kit 0.118.0 : | Build with ALSA support............................... : true | Build with old FireWire (FreeBob) support............. : false | Build with new FireWire (FFADO) support............... : true | Build with OSS support................................ : false | Build with Sun audio support.......................... : false | Build with CoreAudio support.......................... : false | Build with PortAudio support.......................... : false | Build with Celt support............................... : false
Ideally JACK needs to run with realtime privileges. The simplest approach to achieve this is to create a 'realtime'
group with permissions to elevate realtime priority, nice priority and increased locked-in-memory address space rights.
First create the 'realtime' group, then add yourself (or whoever needs the realtime control) to that group.
> groupadd realtime > usermod -aG realtime andy
Next, edit the /etc/security/limits.conf file to provide the realtime group with the new real-time
abilities. The value used for memlock should be half the available physical RAM.
/etc/security/limits.conf@realtime - rtprio 90 @realtime - memlock 1544415 @realtime - nice -5
You will need to log out and back in for these changes to take effect.
Starting the JACK Daemon
It is now possible to start the JACK daemon. The command below starts the daemon with realtime priority using the FFADO FireWire backend.
> jack -R -d firewire
The output should look something like the output below.
jackd 0.118.0 Copyright 2001-2009 Paul Davis, Stephane Letz, Jack O'Quinn, Torben Hohn and others. jackd comes with ABSOLUTELY NO WARRANTY This is free software, and you are welcome to redistribute it under certain conditions; see the file COPYING for details no message buffer overruns JACK compiled with System V SHM support. loading driver .. libffado 2.0.0 built Sep 23 2010 09:05:56 libiec61883 warning: Established connection on channel 0. You may need to manually set the channel on the receiving node. libiec61883 warning: Established connection on channel 1. You may need to manually set the channel on the transmitting node.
Input-Output Example
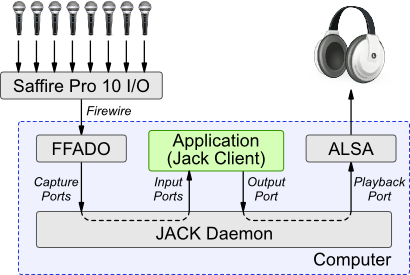
The following program demonstrates the Saffire Pro 10 operating with Linux. The program is a JACK client that captures audio from the Saffire's eight line-in inputs, mixes the signals, then outputs them on the PC's local audio output using ALSA. The diagram below illustrates this setup. In particular it shows how the JACK daemon provides the routing between the Saffire and ALSA output via the test JACK client.
The code can be downloaded using the link below.
The code is compiled using the following command.
> gcc -Wall -ljack -lpthread -lrt -o inOut inOut.c
The JACK installation includes two special clients that provides ALSA support. One provides access to input ports, the other access to outputs. So that this example program can output the mixed signals using ALSA, the output client must be started.
> alsa_out
Next the demonstration client can be started. With something suitable connected to the PC's audio output, you should be able to hear a mix of the inputs connected to the Saffire.
> ./inOut
Crackles and Pops
If you experience some crackling on the audio output, this is probably due to the alsa_out stage. This has quite a
hard job to do as it must align the samples captured from the Saffire to those expected by ALSA; in which there is bound to be some jitter.
The crackle situation can be improved at the expense of latency by using the target_delay option.
> alsa_out -t 1000
The following JACK client can be used to test the quality of the connection from Saffire inputs into JACK. It captures
the Saffire's eight audio inputs and writes them to a wav file called 'capture.wav'. If the recording is crackle free,
then it must be the JACK->>ALSA interface provided by alsa_out that is causing the problem.





